Routing
Policy Routing
MikroTik RouterOS supports policy based routing. Routing can be performed based on:
 |
|
 IP Routes Manual |
Routing Protocols
Routing protocols enable information exchange about routing between routers and eases the network administration. Following routing protocols are supported by MikroTik RouterOS:
|
| RIP Manual OSPF Manual BGP Manual |
Load Balancing
Load Balancing
Load balancing is implemented as equal cost multipath routing. With load balancing two or more gateways can be specified for the same destination. That applies to the default one as well. Equal cost multipath routes can be created by routing protocols (RIP or OSPF), or by adding a static route with multiple gateways. The routing protocols may create routes with equal cost automatically, if the cost of the interfaces is adjusted properly.
|
| IP Routes Manual |
Tunnels and VPN
PPTP (Point to Point Tunnel Protocol)
PPTP (Point to Point Tunnel Protocol) supports encrypted tunnels over IP. The MikroTik RouterOS implementation includes support for PPTP client and server. General applications of PPTP tunnels
|
| PPTP Manual |
EoIP (Ethernet over IP)
Ethernet over IP (EoIP) Tunneling is a MikroTik RouterOS protocol that creates an Ethernet tunnel between two routers on top of an IP connection. When the bridging function of the router is enabled, all Ethernet traffic (all Ethernet protocols) will be bridged just as if there where a physical Ethernet interface and cable between the two routers (with bridging enabled). This protocol makes multiple network schemes possible.
| EoIP Manual |
IPSec (IP Security)
IPsec (IP Security) supports secure (encrypted) communications over IP networks.
| IPSec Manual |
Bridging
Interface Bridging
MikroTik RouerOS supports MAC level bridging of Ethernet packets. Ethernet, Ethernet over IP (EoIP), Prism, Atheros and RadioLAN interfaces are supported. The Bridge Interfaces can also be Firewalled.
|
| Bridge Manual |
Transparent Bridging of Remote LANs
Remote LANs can be transparently bridged over secure VPN connections by means of Ethernet over IP tunnels and Ethernet bridge. One MikroTik Router is required per one remote LAN. The Routers should be able to communicate with each other over public network. Secure VPN tunnels are established between them. EoIP tunnels are run over these VPN connections with bridging between EoIP and LAN interfaces.
|
| EoIP Manual |
Bandwidth Management
Queuing / Bandwidth Management
MikroTik RouterOS supports Class Based Queuing (CBQ) for bandwidth limitation. It is possible to limit just one IP or MAC address, or whole subnet. Queuing can be performed based on:
|
| Bandwidth management Manual |
Bandwith Limiting on PPP Connections
PPP connections and HotSpot can be set for certain bandwidth. Following connections can have bandwidth limiting in MikroTik RouterOS:
|
| General Settings for User Authentication and Accounting HotSpot Manual |
Cache
Web Proxy
The MikroTik RouterOS has the squid proxy server implementation. The web proxy can be used as transparent and normal web proxy at the same time. In transparent mode it is possible to use it as standard web proxy, too. Proxy server features:
|
| Web-Proxy Manual |
DNS Cache
DNS cache is used to minimize DNS requests to an external DNS server as well as to minimize DNS resolution time. This is a simple recursive DNS server with local items. When the DNS cache is enabled, the MikroTik router responds to DNS TCP and UDP requests on port 53.
|
| DNS Client and Cache Manual |
Router and Network Administration
Remote Router Administration
MikroTik RouterOS supports remote access via Telnet and GUI. Files and software packages can be uploaded/downloaded using ftp. The WinBox GUI allows easy real-time router management and monitoring.
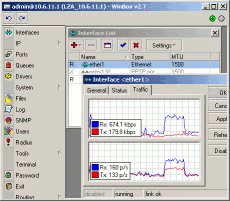 |
|
| Basic Setup Guide |
Network Administration
Mikrotik RouterOS provides vide variety of network administration and monitoring tools. It allows you to easily find out bottlenecks in your system, track down users clogging up your bandwidth, detects intrusion attempts, etc. Following tools by provided with MikroTik RouterOS:
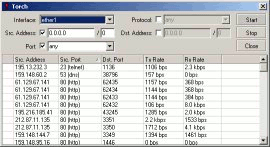 |
|
| Bandwidth Test Torch |
Wireless Setups
Wireless Access Point
MikroTik router with Prism or Atheros wireless card can be configured to be Wireless Access Point. Possible setups are:
 |
|
| Wireless Interface Manual |
Wireless Client
MikroTik router can be used as a wireless client. It can be directly connected to a Base Unit. If you are using MikroTik router for ISP, note that you will be sharing the link with the other clients so the bandwidth will be divided. MikroTik router supports Prism II, Atheros, Aironet and RadioLAN interfaces.
 |
|
| Wireless Interface Manual |
Modem Setups
Dial-In Server
MikroTik router can connect asynchronous modems and serve as dial-in server:
 |
|
| PPP Manual |
Dial-Out
Simply connect a modem to the router via serial interface and it will be possible to dial-up to some ISP.
| PPP Manual |
Modem Pool
MikroTik router supports multiple modem connections. You can connect up to 8 modems using an octopus cable. Users will be able to dial-up to your router with their modems through the telephone line.
|
| PPP Manual |
Firewalling
Filtering rules
Filtering rules is the set of conditions and actions that are applied in a certain order until a decision to route or drop the packet is reached. When a particular packet meets all the conditions specified in a given row of the table, the action is carried out specified in that row (whether to route or drop the packet) is carried out. Rules can be applied to the following :
|
| Firewall Manual |
Peer-2-peer filtering
Peer to peer filtering is made for network administrators that wish to limit traffic amount that is used for p2p programs like Kazaa, emule, DC and others.Wire range of peer to peer protocols are supported.
| P2P Filtering Manual |
Masquerading
Masquerading is used for enabling hosts with local addresses to communicate with other networks using the interface address of the gateway router. So instead of your local address the outside hosts will see gateway's interface address.
| Masquerading Manual |
Network Address Translation (NAT)
NAT is the translation of an IP address used within one network to a different IP address known within another network. You map the local network addresses to one or more outside IP addresses and unmap the global IP addresses on incoming packets back into local IP addresses. This helps ensure security since each outgoing or incoming request must go through a translation process that also offers the opportunity to qualify or authenticate the request or match it to a previous request.
| NAT Manual |
Logging
You can log everything that is going on in your firewall: what actions were performed, what packets dropped or forwarded. This gives you the opportunity to make correct decision about adding new rules.
| Log Management Manual |
HOTSPOT
HotSpot Gateway
Enables easy user authentication and accounting in public, private, wired or wireless networks. HotSpot technology allows Internet providers to offer Internet access to customers, while applying certain Internet use rules and limitations. It is very convenient for Internet cafes, hotels, airports, schools and universities. The Internet provider gets a complete real-time accounting of each customer's time spent on the network, data amount sent, received and more.
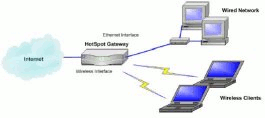 |
|
 HotSpot Manual |
User Management System
MikroTik provides complete solution for hotel hotspot/pppoe user management.
 |
|